checksec
It is not a coincidence that the first post in this still young year is about security. Since I realized last year how far the current internet with its "data capitalism" has strayed from its beginnings, I did a lot of reading to understand the situation in more detail. Data and Goliath by the renowned security expert Bruce Schneier was a depressing eye opener and I am currently still reading his new book Click Here to Kill Everybody which reiterates the problems in light of more recent events. If you are looking for more in depth information from somebody with a long track record, I can strongly recommend those books as a starting point.

One of the lessons I recently learned is that real security is extremely hard to achieve - even by the best in the field. It is also pretty much impossible for a non-specialist to evaluate the security of any given solution without much more transparency into the security design process (threat models) and the implementation methods used to avoid them (protocols, etc.).
The Linux kernel and the GNU tool chains on the other hand offer a variety of hardening features to protect a GNU/Linux system from certain vulnerabilities. Having a tool to quickly evaluation which of those methods are in effect on a given system would be a welcome tool in the toolbox, especially when custom build systems are involved rather than the well known distributions.
The application security expert Tobias Klein provides a nice shell
script to do exactly
that. As checksec.sh only requires the Bourne Again Shell (bash), it is
immediately usable on pretty much every GNU/Linux system out there.
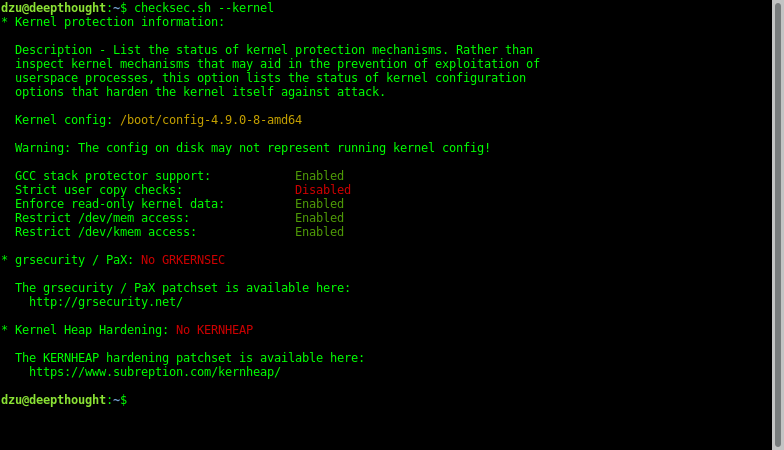
To give you a quick glimpse of what the script does, here is a screenshot of running the kernel checks on a stock Debian 9 GNU/Linux system on an x86_64 system:
Below are the first few items of checking all running processes. It is run through sudo to also check system processes:
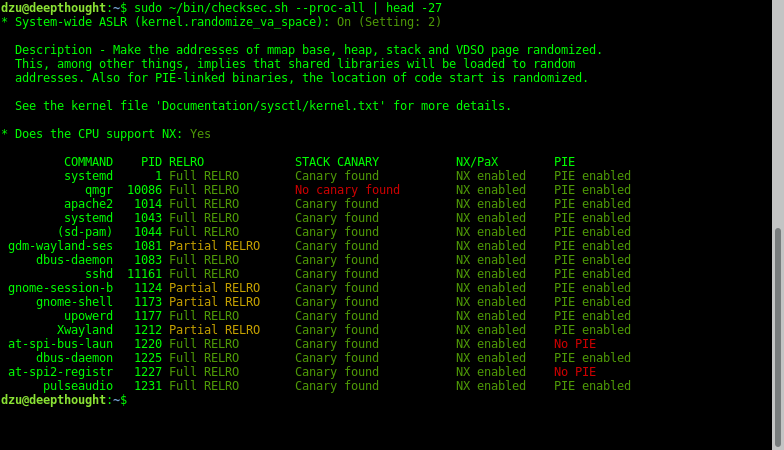
It seems that Debian has a somewhat lax approach to using the available mechanisms.
Of course it is trivial to also quickly check packages not installed from official distribution repositories by whatever means. For example the nice free Teamviewer remote control solution is available through a separate Debian repository:
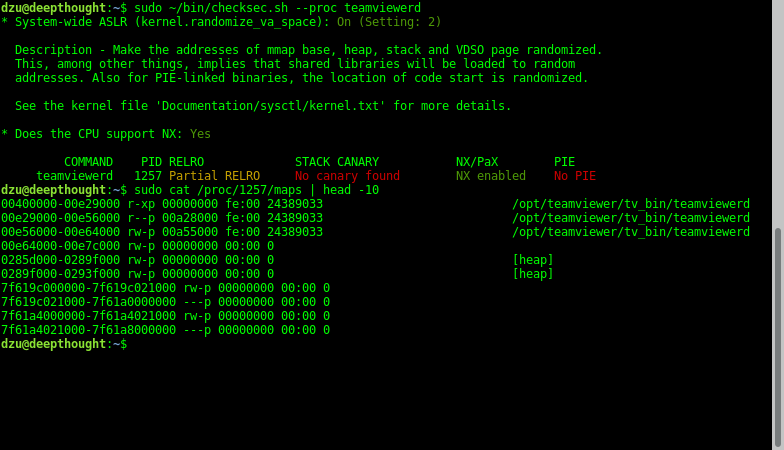
So this binary does not use stack smash protection nor position independent code (PIE). Unfortunately the latter disables the address space layout randomization (ASLR) as can be seen by checking the virtual address space of the process. Especially for such an internet facing service I would love to see those features enabled.
In case you are not familiar with the used terms like "RELRO" and "stack canaries", there is already a good short blog post containing more detailed explanations of the underlying concepts.
Comments
Comments powered by Disqus